As we dive deeper into the digital age, cybersecurity threats continue to evolve in complexity, scale, and impact. In 2025, organizations and individuals face an increasingly hostile cyber landscape driven by sophisticated attackers, emerging technologies, and expanding attack surfaces. From AI-generated phishing to quantum-enabled hacking, the nature of cyber threats is changing rapidly — and staying ahead requires awareness and preparation.
1. AI-Powered Cyberattacks
AI isn’t just a tool for defenders — it’s now a weapon for attackers too. Cybercriminals are using AI to craft more believable phishing emails, automate attacks, evade detection, and exploit vulnerabilities faster than ever.
- Deepfake scams may target executives with realistic audio or video impersonations.
- AI-driven malware can adapt dynamically to avoid security protocols.
- Expect more machine-speed attacks, where threats evolve in real time.
2. Ransomware Evolution
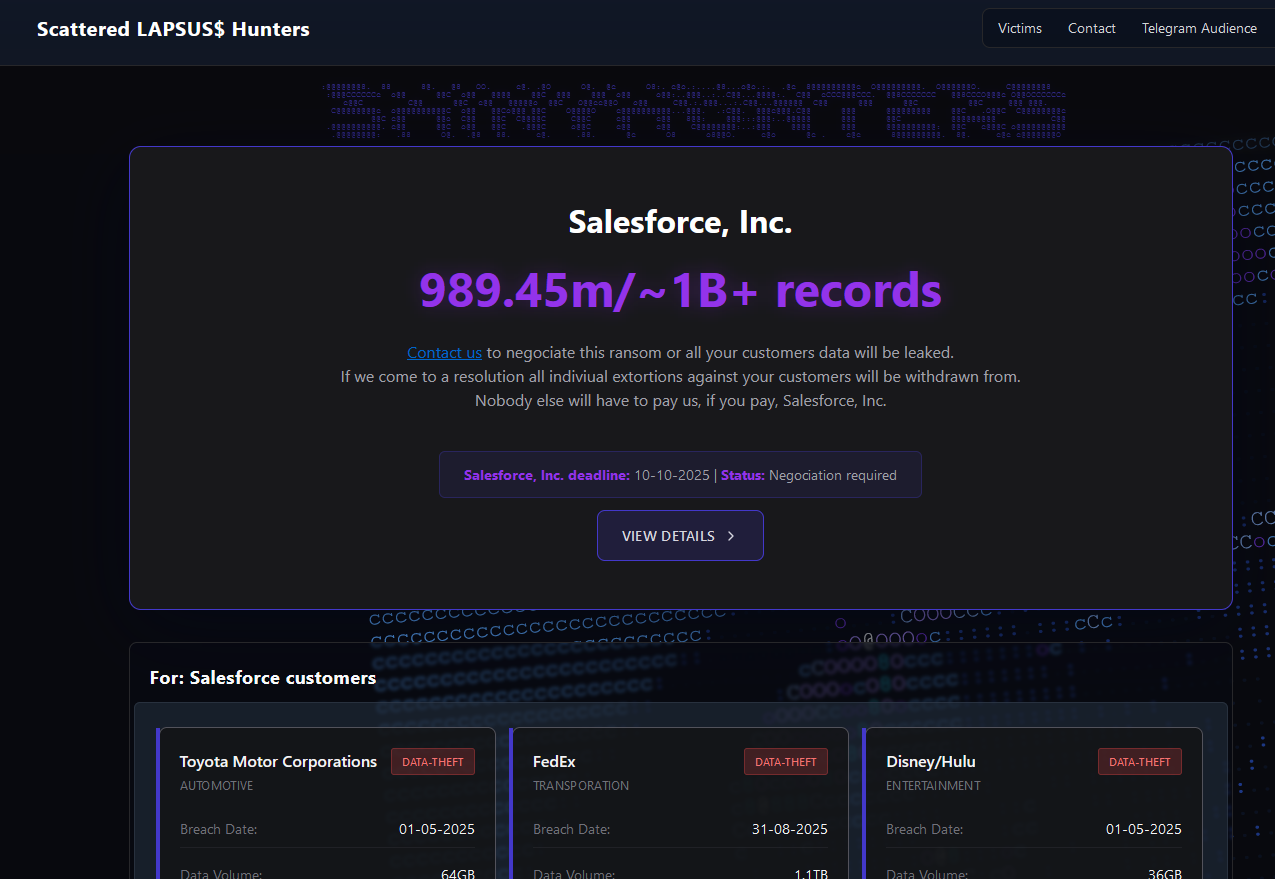
Ransomware continues to be one of the most dangerous and profitable cyberattack methods. In 2025, ransomware groups are evolving with more aggressive tactics:
- Double and triple extortion: Hackers not only encrypt data but also steal and threaten to leak it.
- Targeting critical infrastructure: Healthcare, energy, and government systems are increasingly in the crosshairs.
- Ransomware-as-a-Service (RaaS): Even low-skilled attackers can launch ransomware attacks by renting tools on the dark web.
3. Supply Chain Attacks
Third-party vendors are becoming one of the weakest links in organizational security. In a supply chain attack, threat actors breach a trusted partner to gain indirect access to their real target.
- Notable examples: SolarWinds, Kaseya.
- In 2025, more companies will fall victim to software updates or vendor platforms hijacked by malicious actors.
- Zero-trust frameworks and tighter vendor scrutiny will be crucial.
4. Quantum Threats on the Horizon
Quantum computing isn’t mainstream yet, but it’s advancing fast. Experts warn that once quantum computers reach sufficient power, they could break current encryption methods, exposing sensitive communications and data.
- While not a direct 2025 threat, “harvest now, decrypt later” attacks are already being conducted — where encrypted data is stolen today in anticipation of future quantum decryption.
5. IoT and Smart Device Vulnerabilities
With billions of IoT devices (smart TVs, wearables, industrial sensors) connected to the internet, each becomes a potential entry point for attackers.
- Many devices still lack robust security features.
- Home networks and critical infrastructure are especially vulnerable.
- In 2025, botnets like Mirai could return in new forms, powered by hijacked smart devices.
6. Cloud Security Breaches
As organizations move to the cloud, misconfigured environments and poorly managed access controls remain top risks.
- Multi-cloud environments can introduce complexity and blind spots.
- Stolen credentials, often through phishing, remain the primary cause of cloud breaches.
- Expect more attacks on serverless computing and container orchestration platforms like Kubernetes.
7. Phishing Gets Smarter
Phishing is still one of the most effective methods to breach networks — and it’s getting a major upgrade.
- AI-generated spear phishing emails can mimic writing styles with frightening accuracy.
- Voice phishing (vishing) and video phishing may rise with deepfake technology.
- In 2025, phishing will shift from bulk emails to highly personalized social engineering campaigns.
8. Insider Threats
Not all threats come from outside. In 2025, insiders — malicious or careless — will continue to pose serious risks.
- Employees can unintentionally leak data through shadow IT or weak passwords.
- Disgruntled insiders may abuse access to steal or sabotage data.
- Behavioral analytics tools will be key to detecting suspicious activity early.
9. Credential Stuffing and Identity Attacks
With massive data leaks over the years, attackers have millions of usernames and passwords at their disposal.
- In 2025, credential stuffing attacks — using leaked credentials to access other services — will surge.
- MFA fatigue attacks, where users are bombarded with login requests until they approve, are rising.
- Passwordless authentication (like biometrics or passkeys) will gain momentum as a defense.
10. Hacktivism and Geopolitical Cyberwarfare
As global tensions increase, nation-state-sponsored attacks and politically motivated hacking will become more prominent.
- Critical infrastructure, elections, and media are prime targets.
- In 2025, cyberwarfare tactics will include DDoS attacks, data leaks, and misinformation campaigns.
- Small nations and activist groups may also launch digital protests or disruptions against corporations and governments.
Final Thoughts: Staying Ahead in 2025
Cyber threats in 2025 are more sophisticated, stealthy, and destructive than ever before. Organizations and individuals must evolve their defense strategies by adopting:
- Zero-trust security models
- AI-powered threat detection tools
- Multi-factor authentication and passwordless logins
- Regular training and awareness programs
- Incident response planning and simulation
Cybersecurity is no longer just an IT issue — it’s a business priority, a national security concern, and a personal responsibility.