In today’s connected world, we all want to access our favorite apps and websites without re-entering our password every two seconds. That’s where authentication tokens, or “auth tokens,” come in. Think of them like a digital VIP pass. When you log in with your username and password, the server checks your credentials and, if everything’s good, hands you a special token. Instead of sending your password with every request, your app sends this token. The server then uses the token to confirm you’re still you, and you can access all the cool stuff you’re supposed to.
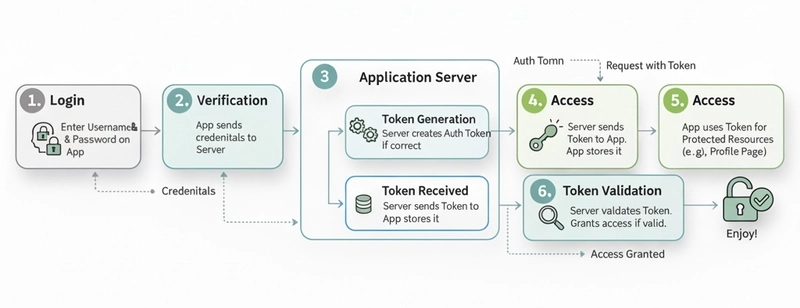
How It Works: A Simple Flow
The basic process is pretty straightforward:
- Login: You enter your username and password on an application’s login screen.
- Verification: The application sends your credentials to its server for verification.
- Token Generation: If your credentials are correct, the server generates a unique auth token.
- Token Received: The server sends this token back to your application, which stores it, usually in a cookie or local storage.
- Access: From now on, whenever you need to access a protected resource, like your profile page or your shopping cart, the application includes the token in the request header.
- Token Validation: The server receives the request, validates the token, and grants access if it’s valid.
This system is great for scalability because the server doesn’t need to remember who is logged in. This makes the server stateless, which is a huge plus for performance and building microservice architectures.
Types of Tokens You’ll Encounter
There are a few different types of tokens, each with its own pros and cons.
1. JSON Web Tokens (JWTs)
A JWT (pronounced “jot”) is a popular type of token that’s self-contained. This means all the necessary user information is right inside the token itself. A JWT is made up of three parts, separated by periods:
- Header: Describes the token type and the signing algorithm.
- Payload: Contains “claims,” which are statements about the user and the token. This is where you’d find user ID, roles, and the token’s expiration date.
- Signature: A unique signature created using a secret key. This is what the server uses to verify that the token hasn’t been tampered with.
Because a JWT contains everything the server needs to know, the server doesn’t have to perform a database lookup for every request. This makes them really fast and efficient.
Here’s a quick Python example using the PyJWT library to create a JWT:
import jwt
import datetime
payload_data = {
'sub': '1234567890',
'name': 'John Doe',
'iat': datetime.datetime.now(datetime.timezone.utc),
'exp': datetime.datetime.now(datetime.timezone.utc) + datetime.timedelta(minutes=30)
}
secret_key = 'your_super_secret_key' # In a real app, use an environment variable!
token = jwt.encode(payload_data, secret_key, algorithm='HS256')
print(token)
You can then decode and verify this token on the server side to get the payload data.
2. Opaque Tokens
Unlike JWTs, opaque tokens are just random strings of characters. The client can’t read anything from them. They are essentially a reference to a record stored in the server’s database. When a server receives an opaque token, it has to go to the database to look up the token and retrieve the associated user data and permissions.
Pros & Cons:
- JWTs: Fast, scalable, and don’t require database lookups. The downside is that once issued, they can’t be easily revoked before they expire.
- Opaque Tokens: More secure since no information is exposed to the client. They are also easily revocable. The trade-off is that they require a database lookup on every request, which can add overhead.
3. Hybrid Tokens
A common and secure pattern is to use a hybrid approach. This combines the best of both worlds. You’ll often see this with OAuth 2.0:
- Short-lived Access Token: This is a JWT, used for accessing resources. It’s valid for a short time (e.g., 15 minutes), so if it’s stolen, the attacker doesn’t have much time to use it.
- Long-lived Refresh Token: This is an opaque token, used to get a new access token once the old one expires. It’s stored securely and can be revoked by the server if needed. This prevents a user from having to log in again every 15 minutes.
This approach balances the performance benefits of JWTs with the security and revocability of opaque tokens.
Conclusion: Which One Should You Use?
The choice of token depends on your application’s needs. For a simple app where you want to keep things fast and stateless, a JWT might be the perfect fit. For a system that requires a high level of security and granular control over token revocation, a hybrid model is often the way to go. No matter which you choose, understanding how they work is a crucial skill for any developer building secure and scalable applications. 💻🔒