This is a submission for the Auth0 for AI Agents Challenge
What I Built
Project Overview
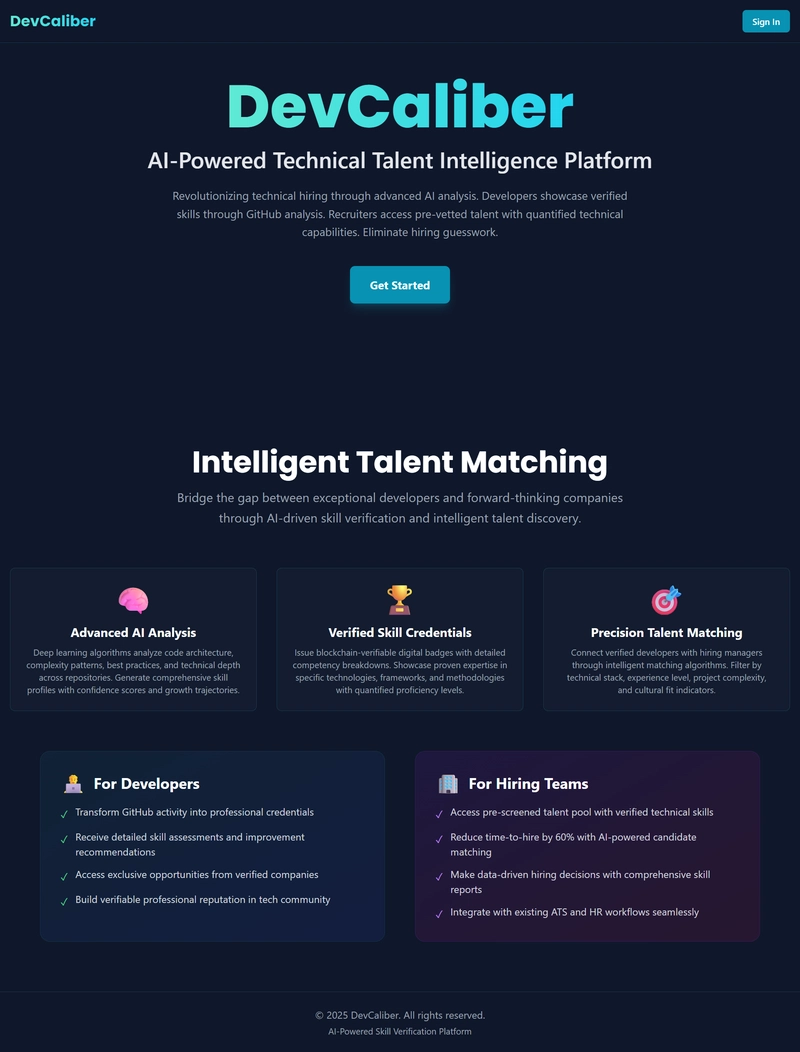
DevCaliber is a secure technical talent platform that aims to revolutionize skills-based hiring through authenticated AI agents and verified developer credentials. Built with Auth0 for AI Agents, it creates a trusted ecosystem where candidates prove their technical abilities through authenticated GitHub analysis, while recruiters can access the verified talent with granular security controls.
Problem It Solves
Modern technical hiring is broken by outdated verification methods and security gaps:
- Degree-Centric Hiring – Companies miss talented developers who lack formal CS degrees but have proven coding skills.
- Resume Fraud – No way to verify claimed technical abilities or project ownership.
- Unsecured AI Systems – AI agents access sensitive hiring data without proper authentication or role restrictions.
- GitHub Profile Spoofing – Candidates can claim ownership of repositories they didn’t create.
- Data Privacy Violations – Hiring platforms expose candidate information to unauthorized users.
- Manual Skill Assessment – Technical interviews consume weeks of engineering time.
DevCaliber solves this through authenticated GitHub ownership verification and Auth0-secured AI agents that provide role-based access to verified technical talent data.
Features and User Flow
🧑💻 For Candidates: Prove Your Skills, Not Your Degree
- Authenticated GitHub Ownership – Auth0 + GitHub OAuth proves repository ownership beyond doubt.
- AI Technical Assessment – Deep analysis of coding patterns, project complexity, and documentation quality.
- Verified Skill Credentials – Timestamped digital badges based on actual code analysis, not self-reported skills.
- Personal Career AI – Get hiring advice, skill gap analysis, and market insights (restricted to candidate’s own data).
- Skills-First Profile – Showcase real projects and verified capabilities to recruiters who value talent over degrees.
👔 For Recruiters: Find Talent by Skills, Not Credentials
- Verified Talent Access – Every candidate has authenticated GitHub ownership and AI-verified skills.
- Skills-Based Discovery – AI agent helps find candidates by actual coding abilities, not just resume keywords.
- Pre-Vetted Talent Pool – Access thoroughly analyzed developer profiles with confidence scores.
- Secure Communication – Direct messaging with candidates, protected by role-based access controls.
- Technical Deep Dive – Review actual code quality, project complexity, and documentation standards of the candidates.
🛡️ For Administrators: Secure Platform Governance
- Recruiter Verification – Manual approval ensures only legitimate hiring professionals can have access to candidate data.
- Platform Security – Monitor all AI agent interactions with comprehensive audit trails.
- Quality Control – They can guide candidates on skill development and help recruiters optimize their search.
- Unlimited AI Access – Full platform oversight with unrestricted AI agent capabilities.
- Data Protection – Ensure sensitive hiring information remains secure across all user interactions.
Demo
Live Site
Site is deployed here: DevCaliber
Project Snapshots
Demo Admin
Demo Recruiter
Demo Candidate
New User:Candidate
Real User: Recruiter
Demo Credentials
🛡️ Admin Account:
• Email: admin@testcredential.com
• Password: 1234test*
• Agent Capabilities: Full platform access, unlimited AI usage, can message all users.
👔 Recruiter Account:
• Email: recruiter@testcredential.com
• Password: 1234test*
• Agent Capabilities: View all candidates, AI talent search, can message candidates only.
🧑💻 Candidate Account:
• Email: candidate@testcredential.com
• Password: 1234test*
• Agent Capabilities: Own profile analysis, career AI advice, receive messages only, can’t message or have access to other candidates’ profiles.
User Flows & Navigation
1. Real User Signup Flow
🏠 Landing Page
↓
[Sign Up Button] → Auth0 Login Screen
↓
Authentication Options:
• Email/Password
• Google OAuth
↓
✅ Successful Authentication
↓
🎯 Role Selection Page
↓
┌─────────────────┬───────────────────────┐
│ 👩💻 Candidate │ 👔 Recruiter │
│ ↓ │ ↓ │
│ ✅ Role Assigned │ 📝 LinkedIn URL │
│ Instantly │ Required │
│ ↓ │ ↓ │
│ 🎯 Candidate │ 📤 Request Sent │
│ Dashboard │ to Admin │
│ ↓ │ ↓ │
│ 📊 Platform │ ⏳ Waiting for │
│ Overview │ Approval Page │
│ ↓ │ ↓ │
│ 🔗 GitHub Auth │ 🚫 Zero Access │
│ Section │ Until Approved │
│ ↓ │ │
│ 🤖 AI Analysis │ │
│ Available │ │
└─────────────────┴────────────────────┘
2. Demo Account Flow
🏠 Landing Page
↓
[Demo Login Button] → Auth0 Login Screen
↓
Email Recognition (Auth0 Actions):
↓
┌─────────────────┬─────────────────┬─────────────────┐
│admin@test... │recruiter@test...│candidate@test...│
│ ↓ │ ↓ │ ↓ │
│🛡️ Admin Role │👔 Recruiter Role│👩💻 Candidate Role│
│ Auto-Assigned │ Auto-Assigned │ Auto-Assigned │
│ ↓ │ ↓ │ ↓ │
│🎯 Admin │🎯 Recruiter │🎯 Candidate │
│ Dashboard │ Dashboard │ Dashboard │
│ ↓ │ ↓ │ ↓ │
│• All Candidates │• All Candidates │• Own Profile │
│• All Recruiters │• AI Agent │• Career AI │
│• Recruiter │• Messaging │• Receive │
│ Requests │ Candidates │ Messages │
│• Unlimited AI │• Limited AI │• Limited AI │
└─────────────────┴─────────────────┴─────────────────┘
3. Candidate GitHub Analysis Flow
👩💻 Candidate Dashboard
↓
📊 GitHub Profile Analysis Section
↓
[Connect GitHub Account] Button
↓
🔗 GitHub Authentication Flow
↓
✅ GitHub Account Connected
↓
👤 Github Profile Saved
• GitHub Username
• Repository Access
↓
[Analyze My Profile] Button
↓
🤖 AI Analysis Process
• Repository Analysis
• Skill Assessment
• Code Quality Review
• Tech Stack Detection
↓
✅ Analysis Complete
↓
📋 Results Displayed:
• Verified Skill Badges
• GitHub Analysis Summary
• Top Repositories
• Competency Scores
↓
🎯 Added to Talent Pool
(Visible to Recruiters)
4. Recruiter Verification Workflow
👔 New Recruiter Signup
↓
🎯 Role Selection: "Recruiter"
↓
📝 LinkedIn Profile Required
[Enter LinkedIn URL] Input Field
↓
✅ LinkedIn URL Submitted
↓
📤 Recruiter Request Created
• User Email
• LinkedIn Profile
• Timestamp
• Status: "Pending"
↓
⏳ Waiting for Approval Page
"Your recruiter request is under review"
↓
🛡️ Admin Reviews Request
(In Admin Dashboard)
↓
┌─────────────────┬────────────────────┐
│ ✅ Approved │ ❌ Rejected │
│ ↓ │ ↓ │
│ 🎯 Recruiter │ 📧 Rejection │
│ Dashboard │ Notification │
│ Access │ ↓ │
│ ↓ │ 🔄 Can Reapply │
│ • All Candidates │ │
│ • AI Agent │ │
│ • Messaging │ │
└─────────────────┴────────────────────┘
5. Admin Approval Process
🛡️ Admin Dashboard
↓
📋 Recruiter Requests Tab
↓
📊 Pending Requests List:
┌─────────────────────────────────┐
│ 👔 John Doe │
│ 📧 john@company.com │
│ 🔗 linkedin.com/in/johndoe │
│ ⏰ Submitted: 2 hours ago │
│ [✅ Approve] [❌ Reject] │
├─────────────────────────────────┤
│ 👔 Jane Smith │
│ 📧 jane@startup.com │
│ 🔗 linkedin.com/in/janesmith │
│ ⏰ Submitted: 1 day ago │
│ [✅ Approve] [❌ Reject] │
└─────────────────────────────────┘
↓
[Approve] Button Clicked
↓
✅ User Role Updated to "Recruiter"
↓
🎯 User Gets Dashboard Access
6. Returning User Flow
🏠 Landing Page
↓
[Sign In Button] → Auth0 Login Screen
↓
✅ Authentication Successful
↓
🔍 Role Check (JWT Claims/localStorage)
↓
┌─────────────────┬─────────────────┬─────────────────┐
│ 🛡️ Admin │ 👔 Recruiter │ 👩💻 Candidate │
│ ↓ │ ↓ │ ↓ │
│ Direct to │ Check Status: │ Direct to │
│ Admin │ ┌─────────────┐ │ Candidate │
│ Dashboard │ │✅ Approved │ │ Dashboard │
│ │ │→ Dashboard │ │ │
│ │ │⏳ Pending │ │ │
│ │ │→ Wait Page │ │ │
│ │ │❌ Rejected │ │ │
│ │ │→ Reapply │ │ │
│ │ └─────────────┘ │ │
└─────────────────┴─────────────────┴─────────────────┘
7. AI Agent Interaction Flows
🤖 AI Agent Access by Role:
👩💻 Candidate Agent:
• “How can I improve my GitHub profile?”
• “What skills should I learn for frontend roles?”
• “Show me my analysis results”
• ❌ Cannot ask about other candidates
• ❌ Cannot send messages
👔 Recruiter Agent:
• “Show me React developers”
• “Find candidates with 3+ years experience”
• “Send message to Demo Candidate: Interview invitation”
• ✅ Access to candidates only
• ❌ Cannot see other recruiters
🛡️ Admin Agent:
• “Show me all platform users”
• “Send message to Demo Recruiter: Platform update”
• “What’s the skill distribution?”
• ✅ Unlimited access
• ✅ Can message anyone
System Architecture
┌─────────────────────────────────────────────────────────────────────────────┐
│ 🌐 CLIENT LAYER │
├─────────────────────────────────────────────────────────────────────────────┤
│ │
│ 📱 React Frontend (Vite + TypeScript) │
│ ┌─────────────────┬─────────────────┬─────────────────┬─────────────────┐ │
│ │ 🏠 Landing │ 🛡️ Admin │ 👔 Recruiter │ 👩💻 Candidate │ │
│ │ Page │ Dashboard │ Dashboard │ Dashboard │ │
│ └─────────────────┴─────────────────┴─────────────────┴─────────────────┘ │
│ ↕️ │
│ 🔐 AuthContext (Role-Based Routing) │
│ ┌─────────────────────────────────────────────────────────────────────┐ │
│ │ • useAuth0 Hook Integration │ │
│ │ • JWT Token Claims Reading │ │
│ │ • Role State Management │ │
│ │ • GitHub User Detection │ │
│ └─────────────────────────────────────────────────────────────────────┘ │
└─────────────────────────────────────────────────────────────────────────────┘
↕️
┌─────────────────────────────────────────────────────────────────────────────┐
│ 🔐 AUTH0 AUTHENTICATION LAYER │
├─────────────────────────────────────────────────────────────────────────────┤
│ │
│ 🏢 Auth0 Tenant │
│ ┌─────────────────┬─────────────────┬─────────────────┬─────────────────┐ │
│ │ 📧 Email/ │ 🔗 GitHub │ 🎯 Auth0 │ 🎫 JWT │ │
│ │ Password │ Social │ Actions │ Tokens │ │
│ │ Auth │ Connection │ (Post-Login) │ + Claims │ │
│ │ │ │ │ │ │
│ │ • Demo Users │ • GitHub OAuth │ • Role │ • Custom │ │
│ │ • Real Users │ • Profile │ Assignment │ Namespace │ │
│ │ │ Extraction │ • User │ • Role Data │ │
│ │ │ │ Metadata │ • User Type │ │
│ └─────────────────┴─────────────────┴─────────────────┴─────────────────┘ │
└─────────────────────────────────────────────────────────────────────────────┘
↕️
┌─────────────────────────────────────────────────────────────────────────────┐
│ 🧠 AI AGENT SECURITY LAYER │
├─────────────────────────────────────────────────────────────────────────────┤
│ │
│ 🎯 RAGService (Fine-Grained Authorization) │
│ ┌─────────────────────────────────────────────────────────────────────┐ │
│ │ Pre-Processing Data Filters │ │
│ │ ┌─────────────┬─────────────┬─────────────┬─────────────────────┐ │ │
│ │ │👩💻 Candidate │👔 Recruiter │🛡️ Admin │🔒 Zero Trust │ │ │
│ │ │ │ │ │ Architecture │ │ │
│ │ │• Own Data │• 16 Cands │• All Data │ │ │ │
│ │ │ Only │ Only │• Complete │• Filter BEFORE AI │ │ │
│ │ │• No Others │• No Other │ Platform │• Context Isolation │ │ │
│ │ │• Career AI │ Recruiters │• Unlimited │• Role-Based Prompts │ │ │
│ │ └─────────────┴─────────────┴─────────────┴─────────────────────┘ │ │
│ └─────────────────────────────────────────────────────────────────────┘ │
│ ↕️ │
│ 🔑 TokenVault (API Management) │
│ ┌─────────────────────────────────────────────────────────────────────┐ │
│ │ • Secure API Key Storage (OpenRouter + Gemini) │ │
│ │ • Role-Based Rate Limiting │ │
│ │ • Admin Unlimited Access │ │
│ │ • Cost Protection & Usage Tracking │ │
│ └─────────────────────────────────────────────────────────────────────┘ │
└─────────────────────────────────────────────────────────────────────────────┘
↕️
┌─────────────────────────────────────────────────────────────────────────────┐
│ 🤖 AI SERVICES LAYER │
├─────────────────────────────────────────────────────────────────────────────┤
│ │
│ 🔄 ChatService (AI Agent Orchestration) │
│ ┌─────────────────┬─────────────────┬─────────────────┬─────────────────┐ │
│ │ 🎯 System │ 📊 Context │ 💬 Messaging │ 📝 Logging │ │
│ │ Prompts │ Building │ Commands │ & Audit │ │
│ │ │ │ │ │ │
│ │ • Role-Based │ • Authorized │ • Role-Based │ • Auth0 User │ │
│ │ AI Behavior │ Data Only │ Recipients │ Context │ │
│ │ • Capability │ • Secure │ • Message │ • AI Usage │ │
│ │ Restrictions │ Context │ Validation │ Tracking │ │
│ └─────────────────┴─────────────────┴─────────────────┴─────────────────┘ │
│ ↕️ │
│ 🌐 External AI APIs │
│ ┌─────────────────┬─────────────────┬─────────────────┬─────────────────┐ │
│ │ 🚀 OpenRouter │ 🧠 Gemini │ 🔗 GitHub │ 💾 LocalStorage│ │
│ │ API │ API │ API │ Services │ │
│ │ │ │ │ │ │
│ │ • Primary AI │ • Fallback AI │ • Profile │ • Messages │ │
│ │ • Rate Limited │ • Cost Backup │ Verification │ • Usage Data │ │
│ │ • Role Aware │ • Same Security│ • Repo Analysis│ • Audit Trail │ │
│ └─────────────────┴─────────────────┴─────────────────┴─────────────────┘ │
└─────────────────────────────────────────────────────────────────────────────┘
GitHub Repository
An AI-Powered Technical Talent Intelligence Platform
An AI-Powered Technical Talent Intelligence Hiring Platform
DevCaliber is a secure technical talent intelligence platform that transforms hiring through Auth0-secured AI agents, delivering
authenticated GitHub ownership verification, AI-verified skill credentials, and role-based talent discovery for enterprise
recruitment. It bridges the gap between authentic technical talent and skills-first recruiters.
🚀 Live Demo
Production Site: DevCaliber
Demo Accounts
-
Admin:
admin@testcredential.compassword:1234test* -
Recruiter:
recruiter@testcredential.compassword:1234test* -
Candidate:
candidate@testcredential.compassword:1234test*
✨ Key Features
For Developers
- Authenticated GitHub Analysis – AI analyzes your verified repositories with skill proficiency scoring and code quality assessment.
- Verified Skill Credentials – Digital badges with timestamps based on actual code analysis, not self-reported skills.
- Professional Profiles – Comprehensive developer portfolios with quantified GitHub metrics and project showcases.
- Recruiter Discovery – Connect with verified, skills-focused recruiters who value talent over degrees.
For Recruiters & Hiring Teams
- Pre-Vetted Talent Pool – Access candidates with AI-verified technical skills and authenticated…
Demo Video
How I Used Auth0 for AI Agents
1. Auth0 React SDK Integration
Auth0 Feature: @auth0/auth0-react with useAuth0 hook.
Functionality: Provides authentication state management and login/logout methods.
Use Case: Centralized authentication for all user types with persistent sessions.
The Auth0Provider wraps the entire application, providing authentication context to all components. The useAuth0 hook gives access to user state, authentication status, and methods to trigger login/logout flows. The configuration includes:
• Domain & Client ID: Identifies your Auth0 tenant and application.
• Redirect URI: Where users return after authentication.
• Scope: Requests access to user profile and email data.
• Audience: Enables JWT tokens for API authorization.
• Refresh Tokens: Maintains sessions across browser restarts.
• Local Storage: Persists authentication state client-side.
// Auth0Provider configuration
// AuthContext.tsx - Using Auth0 hooks
const { user: auth0User, isAuthenticated, isLoading, loginWithRedirect, logout, getIdTokenClaims } = useAuth0();
Why This Matters: Every AI agent interaction requires an authenticated user. This setup ensures secure, persistent authentication across all user sessions while providing the foundation for role-based AI agent authorization.
2. Auth0 Actions (Post-Login Flow)
Auth0 Feature: Server-side Actions triggered after login.
Functionality: Automatic role assignment based on user attributes.
Use Case: Secure, server-side role determination for AI agent authorization.
Auth0 Actions execute server-side after successful login, allowing secure role assignment before the user reaches your application.
This Action:
• Analyzes User Email: Checks for demo account patterns.
• Detects Connection Type: Identifies GitHub social logins.
• Assigns Roles Automatically: No manual role selection needed.
• Sets JWT Claims: Embeds roles directly in authentication tokens.
• Updates User Metadata: Stores role information in Auth0’s database.
The Action runs in Auth0’s secure environment, preventing client-side tampering with role assignment logic.
// Deployed in Auth0 Dashboard
exports.onExecutePostLogin = async (event, api) => {
const { user, connection } = event;
const email = user.email?.toLowerCase();
let userRole="candidate";
// Demo account role assignment
if (email === 'admin@testcredential.com') {
userRole="admin";
} else if (email === 'recruiter@testcredential.com') {
userRole="recruiter";
}
// GitHub users automatically become candidates
if (connection.name === 'github') {
userRole="candidate";
}
// Set custom claims in JWT token
api.idToken.setCustomClaim('https://devcaliber.com/role', userRole);
api.accessToken.setCustomClaim('https://devcaliber.com/role', userRole);
};
Why This Matters: Server-side role assignment prevents users from manipulating their roles client-side. AI agents can trust that roles are authentic and assigned by secure, centralized logic.
3. JWT Token Claims
Auth0 Feature: Custom claims in ID and Access tokens.
Functionality: Embed user roles and metadata directly in JWT tokens.
Use Case: Client-side role verification without additional API calls.
JWT tokens carry user roles as custom claims, eliminating the need for separate API calls to determine permissions. The
implementation:
• Custom Namespace: Uses https://devcaliber.com/ to avoid claim conflicts.
• Role Extraction: Reads roles directly from JWT tokens.
• Type Safety: Validates roles against TypeScript enums.
• Error Handling: Gracefully handles token parsing failures.
• Fallback Logic: Maintains backward compatibility with localStorage.
This approach provides immediate access to user permissions without network requests.
// Reading JWT claims
const getRoleFromToken = async () => {
try {
const tokenClaims = await getIdTokenClaims();
const roleFromToken = tokenClaims?.['https://devcaliber.com/role'];
const userType = tokenClaims?.['https://devcaliber.com/user_type'];
if (roleFromToken && Object.values(UserRole).includes(roleFromToken.toUpperCase() as UserRole)) {
const mappedRole = roleFromToken.toUpperCase() as UserRole;
setRoleState(mappedRole);
}
} catch (error) {
console.error('Error getting token claims:', error);
}
};
Why This Matters: AI agents can immediately determine user permissions from JWT tokens, enabling instant authorization decisions without additional API calls or database queries.
4. Social Connections (GitHub OAuth)
Auth0 Feature: GitHub social connection integration.
Functionality: Seamless GitHub authentication with profile data extraction.
Use Case: Verify GitHub repository ownership for candidates.
GitHub OAuth integration serves dual purposes: Authentication and Repository ownership verification. The system:
• Detects GitHub Users: Identifies users who logged in via GitHub.
• Extracts Username: Gets GitHub username from Auth0 user object.
• Auto-Role Assignment: GitHub users automatically become candidates.
• Repository Verification: Additional verification ensures username authenticity.
• Profile Linking: Connects authenticated GitHub accounts to candidate profiles.
This creates a trusted chain from Auth0 authentication to GitHub repository analysis.
// GitHub user detection
if (auth0User.sub?.includes('github')) {
console.log('GitHub user detected, assigning CANDIDATE role');
setRoleState(UserRole.CANDIDATE);
// Extract GitHub username from Auth0 user object
githubUsername: auth0User.nickname || auth0User.preferred_username
}
// GitHubAuthService.ts - Additional GitHub verification
static async handleCallback(code: string, state: string) {
const storedState = localStorage.getItem('github_auth_state');
if (state !== storedState) {
throw new Error('Invalid state parameter');
}
// Verify GitHub username exists
const userResponse = await fetch(`https://api.github.com/users/${username}`);
return { username: userData.login, email: userData.email };
}
Why This Matters: AI agents analyzing GitHub profiles can trust that repository ownership is verified through Auth0’s secure OAuth flow, preventing profile spoofing and ensuring authentic skill assessments.
5. Token Management & Refresh
Auth0 Feature: Automatic token refresh with secure storage.
Functionality: Maintains authentication state across browser sessions.
Use Case: Persistent login for AI agent interactions.
Token management ensures users remain authenticated during extended AI agent sessions:
• Refresh Tokens: Automatically renew expired access tokens.
• Local Storage: Persists authentication state across browser restarts.
• Secure Logout: Clears all authentication data and redirects appropriately.
• Session Continuity: Users don’t lose progress during long AI conversations.
• Security: Tokens are managed by Auth0’s secure infrastructure.
This prevents authentication interruptions during AI agent interactions.
// Token configuration
useRefreshTokens={true}
cacheLocation="localstorage"
// AuthContext.tsx - Logout with return URL
const signOut = () => {
logout({ logoutParams: { returnTo: window.location.origin } });
setRoleState(null);
};
Why This Matters: AI agent conversations can be lengthy. Automatic token refresh ensures users maintain authenticated sessions without interruption, providing seamless AI interactions.
6. Role-Based Access Control (RBAC)
Auth0 Feature: User metadata and custom claims for authorization.
Functionality: Fine-grained permissions for AI agents based on user roles.
Use Case: Different AI agent capabilities per user type.
RBAC creates distinct AI agent experiences based on user roles:
• Data Filtering: Each role sees different data sets before AI processing.
• Permission Boundaries: Strict enforcement of what each role can access.
• Zero-Trust Architecture: Data filtered at source, not after AI generation.
• Role Isolation: Candidates can’t see other profiles, recruiters see limited pools.
• Admin Override: Complete platform access for administrative functions.
The RAG service filters data BEFORE sending to AI, ensuring no unauthorized information leakage.
// Role-based data filtering
export class RAGService {
static getAuthorizedData(permissions: UserPermissions) {
const { userRole, userEmail } = permissions;
if (userRole === 'candidate') {
// Candidates only see their own data
const userCandidate = mockCandidates.find(c => c.email === userEmail);
return { candidates: userCandidate ? [userCandidate] : [], recruiters: [] };
}
if (userRole === 'recruiter') {
// Recruiters see limited candidate pool
return { candidates: mockCandidates.slice(0, 16), recruiters: [] };
}
if (userRole === 'admin') {
// Admins see everything
return { candidates: mockCandidates, recruiters: mockRecruiters };
}
}
}
Why This Matters: AI agents operate within strict permission boundaries defined by Auth0 roles. This prevents data leakage and ensures each user type gets appropriate AI capabilities without security risks.
7. API Authentication & Rate Limiting
Auth0 Feature: Secure API key management with user context.
Functionality: Role-based rate limiting for AI API calls.
Use Case: Prevent API abuse while giving admins unlimited access.
The TokenVault manages AI API access with Auth0-aware rate limiting:
• Secure Key Storage: API keys stored in environment variables, not code.
• Role-Based Limits: Different usage quotas per user role.
• Admin Privileges: Unlimited access for platform management.
• Cost Protection: Prevents expensive API abuse.
• Usage Tracking: Monitors consumption per user and role.
• Session Management: Separate limits for sessions and daily usage.
This creates a secure, cost-effective AI API management system.
// Auth0-aware rate limiting
class TokenVault {
checkChatLimit(userEmail: string, userRole: string, isAdmin: boolean = false): RateLimitResult {
// Admins (verified by Auth0 claims) have unlimited access
if (userRole === 'admin' || isAdmin) {
return { allowed: true, remaining: { session: 999, daily: 999 } };
}
// Regular users have limits
const sessionRemaining = this.SESSION_LIMIT - data.sessionUsage;
const dailyRemaining = this.DAILY_LIMIT - data.dailyUsage;
return { allowed: true, remaining: { session: sessionRemaining, daily: dailyRemaining } };
}
recordChatUsage(userEmail: string, userRole: string, isAdmin: boolean = false): void {
if (userRole === 'admin' || isAdmin) return; // No tracking for admins
const data = this.getUserData(`tokenVault_${userEmail}`);
data.sessionUsage++;
data.dailyUsage++;
localStorage.setItem(`tokenVault_${userEmail}`, JSON.stringify(data));
}
}
Why This Matters: AI API calls are expensive and can be abused. Auth0-verified roles enable appropriate usage limits while ensuring admins have unlimited access for platform management tasks.
8. Authentication Logging & Audit Trail
Auth0 Feature: Built-in authentication event logging.
Functionality: Automatic audit trail for all login/logout events.
Use Case: Security monitoring and compliance for AI agent access.
Comprehensive logging creates an audit trail for all AI agent interactions:
• Auth0 Native Logging: Automatic tracking of all authentication events.
• AI Interaction Logs: Every AI query logged with user context.
• Message Audit Trail: All inter-user communications tracked.
• Role-Based Monitoring: Different logging levels per user type.
• Security Compliance: Meets audit requirements for AI system access.
• User Attribution: Every action tied to authenticated Auth0 user.
This provides complete visibility into AI agent usage patterns and security events.
// AI interaction logging with Auth0 context
export async function sendMessage(messages: ChatMessage[], context: ChatContext): Promise {
console.log(`🤖 AI Request: ${context.userRole} (${context.userEmail})`);
// Check Auth0-verified role permissions
const rateLimitCheck = TokenVault.checkChatLimit(context.userEmail, context.userRole);
if (!rateLimitCheck.allowed) {
console.log(`🚫 Rate limit exceeded: ${context.userEmail}`);
return 'Rate limit exceeded. Please try again later.';
}
// Record usage with Auth0 user context
TokenVault.recordChatUsage(context.userEmail, context.userRole);
console.log(`✅ AI Usage recorded: ${context.userRole} - ${context.userEmail}`);
}
// MessagingService.ts - Message audit with Auth0 user IDs
static sendMessage(from: string, to: string, content: string): boolean {
const newMessage: Message = {
id: `msg_${Date.now()}_${Math.random().toString(36).substr(2, 9)}`,
from, // Auth0 user email
to, // Auth0 user email
content,
timestamp: new Date().toISOString(),
read: false
};
console.log(`📧 Message logged: ${from} → ${to}`);
return true;
}
Why This Matters: Complete audit trails are essential for AI systems handling sensitive hiring data. Auth0’s built-in logging combined with application-level tracking provides comprehensive security monitoring and compliance capabilities.
Lessons Learned and Takeaways
Overall Experience
Building DevCaliber was my deep dive into the complex world of AI agent security and authentication. This wasn’t just about adding Auth0 to a React app, it was about fundamentally rethinking how AI agents should access and process data based on user roles & permissions. This project pushed me into uncharted territory where traditional authentication patterns don’t quite fit, and I had to architect solutions for problems I’d never encountered before.
Challenges Faced
1. GitHub Social Connection Nightmare
Challenge: After setting up GitHub as a social connection in Auth0 Dashboard (which was straightforward), users kept getting
redirected to the landing page instead of their dashboards after successful GitHub authentication.
The Struggle: I’d to spend a long time debugging redirect flows, thinking it was a routing issue. The Auth0 documentation wasn’t immediately clear about handling post-authentication redirects with social connections, especially when you need role-based routing.
Solution: The breakthrough came when I realized I needed to handle the authentication state properly in the AuthContext and implement proper role detection before redirecting:
// The solution that finally worked
useEffect(() => {
const getRoleFromToken = async () => {
if (isAuthenticated && auth0User) {
// GitHub users automatically become candidates
if (auth0User.sub?.includes('github')) {
console.log('GitHub user detected, assigning CANDIDATE role');
setRoleState(UserRole.CANDIDATE);
return;
}
// Handle other role assignments...
}
};
getRoleFromToken();
}, [isAuthenticated, auth0User]);
Lesson: Always read the Auth0 docs thoroughly. The redirect handling is nuanced and requires understanding the authentication lifecycle well.
2. Role-Based Routing Logic
Challenge: Getting users to the right dashboard based on their role seemed simple in theory but was incredibly tricky in practice.
The Struggle: I tried multiple approaches – localStorage checks, immediate redirects, complex state management. Nothing felt clean or reliable. Users would sometimes see the wrong dashboard briefly, or get stuck in redirect loops.
Solution: The current implementation was honestly something I stumbled upon after trying everything else. The key was letting Auth0 Actions handle role assignment server-side, then reading JWT claims client-side:
// App.tsx - The role routing that finally worked
const renderDashboard = () => {
if (!role) return
Lesson: Sometimes the solution isn’t elegant, it’s what works. Don’t overthink role routing; let Auth0 handle the heavy lifting server-side.
3. AI Agent Data Scoping – The Big Learning Curve
Challenge: This was my first time implementing role-based access control for AI agents. Initially, I was filtering data AFTER getting it from the database, which was both inefficient and potentially insecure.
The Evolution: My first approach was naive:
// BAD: My initial approach
const allCandidates = getAllCandidates();
const filteredForUser = allCandidates.filter(candidate =>
userCanAccess(candidate, userRole)
);
The Breakthrough: I realized I needed to filter data BEFORE it even reaches the AI:
// GOOD: Current pre-processing approach
export class RAGService {
static getAuthorizedData(permissions: UserPermissions) {
if (userRole === 'candidate') {
// Only get the user's own data from the start
const userCandidate = mockCandidates.find(c => c.email === userEmail);
return { candidates: userCandidate ? [userCandidate] : [] };
}
// Role-specific data from the beginning
}
}
Lesson: Data scoping for AI agents is fundamentally different from traditional web apps. Filter at the source, not at the display layer.
4. Smart AI Agents Beyond Q&A
Challenge: Modern AI agents aren’t just chatbots, they need to perform actions like sending messages between users. Implementing the messaging feature using localStorage was trickier than expected.
The Implementation:
// AI-triggered messaging
static sendMessage(from: string, to: string, content: string): boolean {
const newMessage: Message = {
id: `msg_${Date.now()}_${Math.random().toString(36).substr(2, 9)}`,
from, to, content,
timestamp: new Date().toISOString(),
read: false
};
messages.push(newMessage);
localStorage.setItem(this.STORAGE_KEY, JSON.stringify(messages));
return true;
}
Lesson: AI agents today need to be action-oriented, not just conversational. Plan for complex interactions from the start.
5. Badge Generation Cost Management
Challenge: I originally used Gemini 2.5 Flash for image-based badge generation, but my free credits depleted faster than expected.
The Pivot: Had to switch to pre-generated badge images with text info:
// Current badge system
const badgePath = `public/skill-badges/${skill === 'JavaScript' ? 'JS' : skill}-${level.toLowerCase()}.png`;
Lesson: Always have a cost management strategy for AI services. Credits can disappear quickly during development.
What I Learned About AI Agents, Authentication, and Development
1. AI Agents Need Authentication Architecture, Not Just User Auth
Traditional authentication secures users; AI agent authentication secures what the AI can see and do on behalf of users. This requires a completely different mindset, you’re not just protecting routes, but you’re protecting data contexts and AI capabilities.
2. Pre-Processing Security is Non-Negotiable
Filtering AI responses after generation is like closing the barn door after the horse has bolted. The AI has already “seen” unauthorized data. Pre-processing data filters ensure the AI never encounters data it shouldn’t process.
3. Role-Based Rate Limiting is Essential
// TokenVault.ts - Different limits per role
checkChatLimit(userEmail: string, userRole: string): RateLimitResult {
if (userRole === 'admin') {
return { allowed: true, remaining: { session: 999, daily: 999 } };
}
// Regular users get limited access
}
AI API calls are expensive. Role-based limits prevent abuse while ensuring admins can manage the platform effectively.
4. Context Isolation Prevents Accidental Data Leakage
Each user role needs completely separate AI contexts. A recruiter’s AI should never accidentally reference admin data, even if it exists in the system. This requires careful prompt engineering and data scoping.
Key Insights and Advice for Other Developers
1. Read the Docs First (Seriously)
I cannot stress this enough- thoroughly read all documentation for the services you’re integrating. Auth0’s social connection docs, GitHub OAuth flows, AI API services documentation. I could have saved so much debugging if I’d done this upfront instead of diving straight into coding.
2. Design Security Architecture Early
Don’t bolt on authentication later. Design your AI agent architecture around security principles from Day one. Every AI interaction should be authenticated and authorized before processing.
3. Test Role Boundaries Obsessively
Create comprehensive test scenarios for each user role. I spent significant time ensuring hardcoded candidate profiles were consistent across admin and recruiter views. Role restrictions must be enforced at every level – data access, AI responses, UI capabilities.
4. Plan for AI Service Failures
// ChatService.ts - Fallback implementation
if (!response.ok) {
console.log('OpenRouter failed, falling back to Gemini API');
// Fallback to Gemini...
}
AI services fail, hit rate limits, or change pricing. Always have fallback mechanisms to maintain a seamless user experience.
5. Monitor Everything
AI agents can behave unpredictably. Comprehensive logging of authentication events, AI interactions, and data access patterns becomes crucial for debugging and security auditing.
6. User Experience Still Matters
Security shouldn’t destroy usability. Auth0’s seamless authentication flows allowed me to build robust security while maintaining an intuitive user experience. Don’t sacrifice UX for security; find solutions that provide both.
DevCaliber has taught me that building secure AI agents is fundamentally different from traditional web development. It’s not just about protecting routes, it’s about protecting intelligence itself. Auth0 for AI Agents provides the foundation, but the real work is in architecting systems where AI agents respect user permissions at every level of data processing.
This was my first deep dive into AI agent security, and honestly, it was harder than I expected. But the lessons learned here will shape how I approach AI development going forward.
Thank You
Building DevCaliber has been one of the most rewarding experiences of my development journey lately. This project pushed me far beyond my comfort zone, into territories I’d never explored before.
To the Auth0 team: Thank you for creating such powerful tools for developers. Auth0 for AI Agents didn’t just solve my authentication needs; it opened my eyes to what’s possible when security and AI work together seamlessly. The documentation, while sometimes dense(for me atleast), ultimately guided me through concepts I never thought I’d understand.
To my future self: Remember this feeling. Remember the frustration of GitHub OAuth redirects that wouldn’t work, the satisfaction of finally getting role-based AI agents right, and the moment when everything clicked together. Remember that the hardest problems often lead to the most meaningful solutions.
This project has taught me that building secure AI systems isn’t just about code, it’s about reimagining how we think about
authentication, authorization, and user trust in an AI-powered world. DevCaliber started as an idea to help developers showcase their skills, but it became something much bigger.
To everyone reading this: If you’re hesitating to tackle that complex project, to integrate that intimidating service, or to participate in that hackathon- just do it. The learning curve is steep, the debugging sessions are long, but the growth is immeasurable.
Thank you for taking the time to explore DevCaliber. Whether you’re a judge, fellow developer, or someone curious about AI agent security, I hope this project inspires you to build something that pushes your own boundaries.
The future of AI is secure, authenticated, and built by developers who aren’t afraid to tackle hard problems.
“Built with determination,
debugged with patience,
and deployed with hope.”– Divya Singh
October 2025