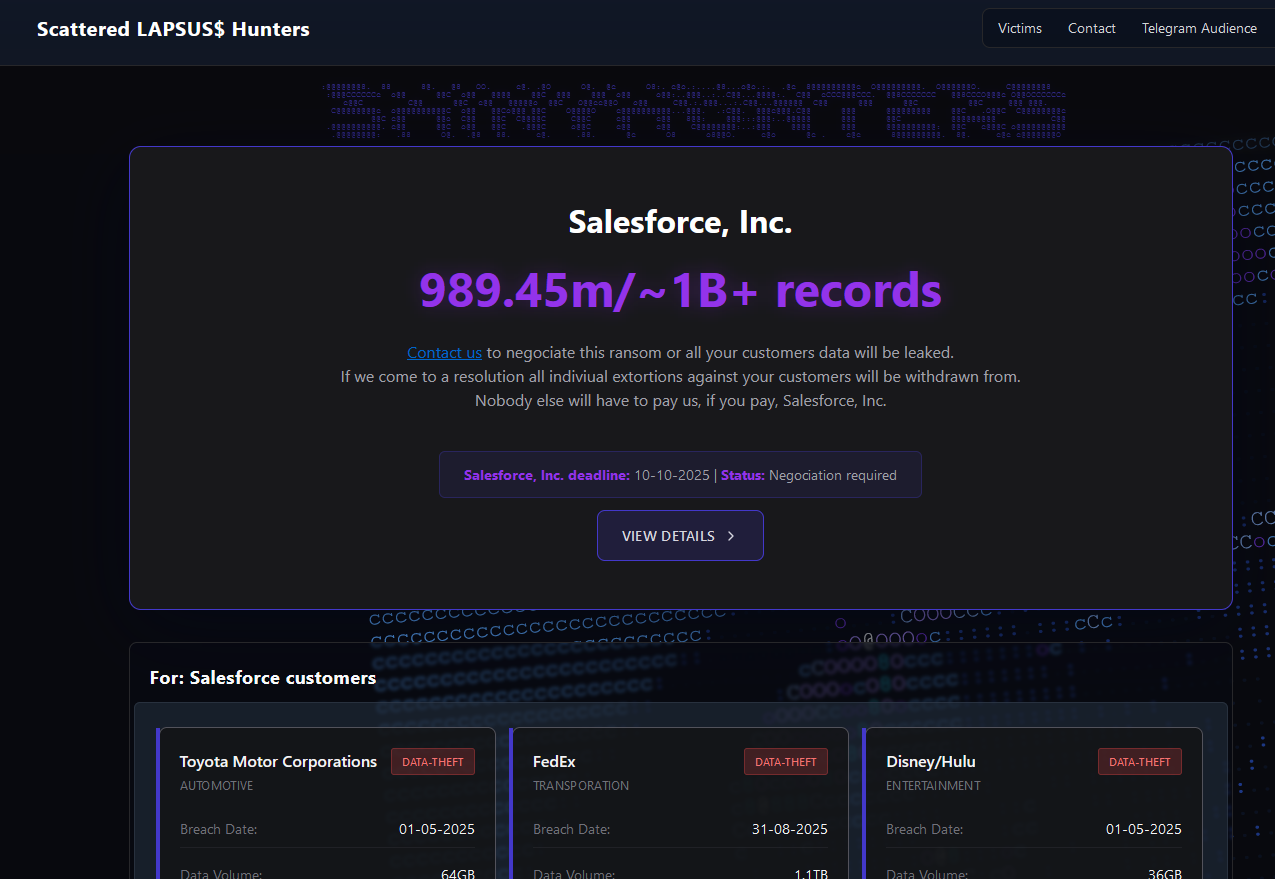
As we progress into an increasingly digital world, cybersecurity continues to be one of the most critical concerns for governments, businesses, and individuals. With the exponential rise in online activities, data generation, and smart devices, the risks and sophistication of cyber threats have also evolved. Cybersecurity in 2025 is no longer just about installing antivirus software—it’s about staying a step ahead of dynamic and intelligent threats.
In this blog, we will explore the key cybersecurity trends, emerging threats, and strategies you must be aware of to stay protected in 2025 and beyond.
🔐 Why Cybersecurity Matters More Than Ever
The digital shift across industries has made every organization—big or small—a potential target. In 2025:
- Over 75% of the global population is expected to be connected to the internet.
- IoT (Internet of Things) devices are projected to exceed 30 billion globally.
- Businesses are rapidly moving to cloud-first infrastructures.
- AI and automation are part of everyday operations.
This means more data, more attack surfaces, and more opportunities for cybercriminals.
🔍 Top Cybersecurity Trends in 2025
1. AI-Powered Cyber Defense
Artificial Intelligence and Machine Learning are revolutionizing cybersecurity. In 2025, advanced AI systems are being used to:
- Detect and respond to threats in real time.
- Monitor network behavior for anomalies.
- Automate routine security tasks like patch management.
However, the same AI is also used by hackers to automate phishing, create convincing deepfakes, and breach defenses faster than ever.
2. Zero Trust Architecture (ZTA)
“Never trust, always verify” is the motto of Zero Trust. Traditional security models are failing in modern networks due to remote work, cloud computing, and mobile devices. Zero Trust enforces:
- Strict identity verification for every user and device.
- Least-privilege access control.
- Continuous monitoring of user behavior.
In 2025, ZTA has become a security standard across enterprises and government networks.
3. Quantum Computing and Post-Quantum Cryptography
Quantum computers, though still developing, have the potential to break today’s encryption methods. As a result:
- Post-quantum cryptography (PQC) is being rapidly adopted.
- Organizations are investing in quantum-resistant algorithms to secure their data for the future.
Being “quantum-safe” is no longer optional—especially for financial institutions and defense sectors.
4. Cloud Security Becomes Paramount
With most organizations adopting multi-cloud or hybrid cloud environments, cloud security is a major focus in 2025. Key developments include:
- Cloud-native security tools integrated into platforms like AWS, Azure, and Google Cloud.
- Better container security for services using Kubernetes and Docker.
- Data governance policies enforced by AI for cloud data traffic.
5. Rise of Cyber Insurance
As data breaches become more common, cyber insurance is now a mainstream risk management tool. In 2025:
- Companies are required to meet strict cybersecurity standards to qualify for coverage.
- Insurers use AI to assess risk levels.
- Policies include coverage for ransomware, legal costs, and reputation damage.
⚠️ Major Cyber Threats You Should Know
1. Ransomware 2.0
Ransomware attacks are now highly targeted, automated, and often involve double extortion—stealing data before encrypting it. Key targets include:
- Healthcare
- Education
- Government infrastructure
- Financial institutions
Ransomware-as-a-Service (RaaS) platforms allow anyone to launch attacks for a fee, making it accessible to low-skill criminals.
2. Deepfakes and Social Engineering
AI-generated deepfakes are being used to:
- Impersonate executives (CEO fraud)
- Create fake videos for blackmail
- Manipulate social media and elections
In 2025, social engineering isn’t just phishing emails—it includes voice clones, fake Zoom calls, and sophisticated identity manipulation.
3. IoT Attacks
Smart home devices, industrial machines, medical sensors, and even vehicles are connected to the internet. Hackers target:
- Smart homes for personal data
- Factories for industrial sabotage
- Connected cars for remote hijacking
IoT devices often lack strong security, making them an easy entry point for attackers.
4. Supply Chain Attacks
One of the most dangerous attack vectors in 2025. Instead of attacking a company directly, hackers compromise third-party vendors or software providers (as seen in the SolarWinds hack). The impact?
- Widespread disruption across multiple organizations
- Harder detection and delayed responses
- Trust erosion between partners
5. Attacks on Critical Infrastructure
Cyberattacks now target power grids, water supplies, transport systems, and even satellites. These threats are often politically motivated and classified as cyber warfare. Nations must now secure both their military and civilian digital infrastructure.
🔧 Protective Measures for 2025
For Individuals:
- Use MFA (Multi-Factor Authentication): Never rely on passwords alone.
- Update Devices Regularly: Install patches and updates as soon as they’re available.
- Avoid Public Wi-Fi: Use VPNs when connecting to untrusted networks.
- Think Before You Click: Phishing emails are more convincing than ever.
- Limit Data Sharing: Don’t overshare personal information online.
For Businesses:
- Conduct Regular Security Audits
- Implement ZTA (Zero Trust Architecture)
- Invest in Employee Training: Human error remains the biggest vulnerability.
- Develop Incident Response Plans
- Backup Data Frequently: Use both offline and cloud backups.
📈 The Future Outlook
Looking ahead, cybersecurity will become deeply integrated into product design, business strategy, and national defense. As new technologies like augmented reality, smart cities, and brain-computer interfaces emerge, so do new vulnerabilities.
We may also see:
- Biometric authentication becoming standard
- Global cybersecurity treaties between nations
- AI-driven security orchestration platforms
- Ethical hackers playing a central role in cyber defense
🧠 Conclusion
Cybersecurity in 2025 is not just about protecting data—it’s about preserving trust, privacy, and functionality in a digital-first world. With every innovation comes a new threat, and the need for proactive, intelligent, and adaptive security measures is more critical than ever.
Whether you’re a student, developer, business owner, or policy-maker, understanding cybersecurity trends and threats is essential to navigating the future safely. Stay informed, stay cautious, and most importantly