Preamble:
This space will be utilized to synthesize my notes and help improve my learning process while I study for the CompTIA Network+ N10-009 certification exam. Please follow along for more Network+ notes and feel free to ask any questions or, if I get something wrong, offer suggestions to correct any mistakes.
For large organizations, simply using a single network isn’t efficient. It can lead to poor performance and security risks. This is why we break down large networks into smaller segments called subnets. We also use a system of public versus private addressing to determine how devices connect to the Internet. Understanding these concepts is essential for a career in networking.
Let’s dive into some of the more advanced concepts of IPv4 addressing.
The Original Classful Addressing Scheme
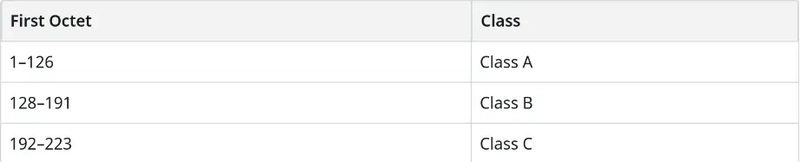
Before we used flexible network masks to define networks, we used a system called classful addressing. This scheme, developed in the 1980s, determined a network’s size based on the first octet of its IP address.
There were three main classes:
- Class A: Reserved for a few very large networks. There are only 126 Class A networks, but each can support over 16 million hosts.
- Class B: A middle ground, with about 16,000 networks, each supporting up to 65,000 hosts.
- Class C: Designed for small networks. There are over two million Class C networks, but each can only support 254 hosts.
Note: The IP ranges 0.0.0.0/8 and 127.0.0.0/8 are also part of Class A but are reserved for special uses. 0.0.0.0/8 refers to “this” network, and 127.0.0.0/8 is used for loopback addressing.
While modern networks primarily use classless addressing with masks, the old classes are still used to describe the most common network masks:
-
Class A:
255.0.0.0(/8) -
Class B:
255.255.0.0(/16) -
Class C:
255.255.255.0(/24)
Classful addressing is also important because it established some IP address ranges that cannot be used on the public Internet.
Public vs. Private Addressing
A public IP address is one that can connect to other public networks over the Internet. Public IP addresses are globally unique and are allocated by organizations like IANA and ISPs.
Most local area networks (LANs) use private IP addresses because they are non-routable over the Internet. This means they cannot be directly reached from outside the local network. Any organization can use private addresses on its networks without having to register them.
The Internet Engineering Task Force (IETF) has reserved the following address ranges for private use:
-
10.0.0.0 - 10.255.255.255(10.0.0.0/8) -
172.16.0.0 - 172.31.255.255(172.16.0.0/12) -
192.168.0.0 - 192.168.255.255(192.168.0.0/16)
Devices on a private network can still access the Internet through a router that uses Network Address Translation (NAT) or a proxy server. These methods translate the private IP addresses to a public IP address before sending traffic to the Internet.
Other Reserved Addresses
There are a few other classes of IP addresses you should know about:
-
Class D (
224.0.0.0/4): Used for multicasting, which allows one device to send data to a group of multiple recipients. -
Class E (
240.0.0.0/4): Reserved for experimental use and testing.
A loopback address is a special address in the 127.0.0.0/8 range, with 127.0.0.1 being the most common. It’s used to check if TCP/IP is correctly installed on a host. Packets sent to this address loop back to the device’s own TCP/IP stack without ever leaving the network adapter. The loopback address is also associated with the hostname localhost.
IPv4 Network Scheme Design
When planning an IPv4 network, you must consider:
- The number of subnets needed and the number of hosts each subnet must support.
- The addresses used must be valid public or private addresses (not from reserved ranges).
- No host ID can have all ‘1’s (reserved for the broadcast address) or all ‘0’s (reserved for the network address).
- Every host ID must be unique on its subnet.
- Every network ID must be unique on the Internet (if using public IPs) or within your internal network (if using private IPs).
When you’re doing subnet calculations, remember that each power of 2 is double the previous one. This is key to finding the number of hosts or subnets available.
Also memorize the decimal values for the number of bits set to 1 in an octet within a mask:
The Subnetting Process
Let’s walk through an example of subnetting the network 172.30.0.0/16.
- Determine how many subnets are required. Let’s say you need 12 subnets. The next power of 2 is 16, which is 24. This means you need to “borrow” 4 bits from the host portion of the address.
-
Calculate the new subnet mask. The default mask for a /16 network is
255.255.0.0. By borrowing 4 bits, the new prefix becomes/20(16 + 4). The new subnet mask is255.255.240.0. -
Check the number of hosts per subnet. With a
/20prefix, you have 12 bits left for the host ID (32 total bits – 20 network bits = 12 host bits). This allows for 212−2=4,094 usable hosts per subnet. (Remember to subtract 2 for the network and broadcast addresses). -
Find the subnet addresses. To find the subnet addresses, you can use the “block size” method. The block size is 256 minus the last non-zero octet in the subnet mask. In our example,
256 - 240 = 16. The first subnet starts at172.30.0.0, the second at172.30.16.0, the third at172.30.32.0, and so on. -
Determine the host ranges. The first usable host address is the subnet address plus 1. The last usable host address is the next subnet’s address minus 2. For the
172.30.16.0/20subnet, the usable host range is172.30.16.1to172.30.31.254.
Classless Inter-Domain Routing (CIDR)
Classless Inter-Domain Routing (CIDR) was developed to solve the problem of public IP addresses running out and to reduce the size of routing tables. CIDR uses the “slash notation” (/16, /24, etc.) and allows multiple networks to be summarized into a single entry for external routers. This is also known as supernetting.
For example, a company might be assigned four contiguous Class C networks: 198.51.100.0, 198.51.101.0, 198.51.102.0, and 198.51.103.0. Using CIDR, you can “supernet” these four networks into a single, larger network by using a shorter prefix. By looking at the binary, you can see that the first 22 bits are the same for all four networks. The new supernet prefix becomes /22. External routers only need one entry for 198.51.100.0/22, which significantly reduces the size of their routing tables.
Variable Length Subnet Masks (VLSM)
Variable Length Subnet Masks (VLSM) is a complementary technique that allows a network designer to use different-sized subnet masks within the same network. This is a much more efficient use of the limited IPv4 address space.
Without VLSM, you would have to use the same size subnet for every network segment, leading to many wasted IP addresses. VLSM allows you to create small subnets for point-to-point links (like those between two routers) and larger subnets for departments with many computers.
Here is an example of a VLSM design based on host requirements:
To create this design, you start with the largest host requirement first.
- Sort the subnets by host size. Start with the largest group of hosts.
-
Determine the required bits. For a group of 80 hosts, you need 7 host bits (27−2=126). This requires a
/25mask (32 – 7 = 25). -
Find the next largest subnet and repeat the process. For 30 hosts, you need 5 bits, but for safety, you’d likely use 6 bits (26−2=62), requiring a
/26mask. -
Assign the remaining subnets. For point-to-point links, which only need 2 hosts, you can use 2 host bits (22−2=2), which requires a
/30mask.
This design ensures that IP addresses are allocated efficiently, reducing waste and allowing for more flexible network design.
You’ve now got a solid grasp of IPv4 addressing. The most effective way to make these concepts stick is to practice them! Grab a pen and paper, or open a calculator, and try converting a few more IP addresses from binary to decimal and back again.
As you prepare for the CompTIA Network+ exam, remember that every complex networking concept is built on these foundational ideas. Keep building on this knowledge, and you’ll be well on your way to becoming a networking pro. Good luck!
QUICK NOTE
This will be my last set of notes using the CompTIA Certmaster course as my main source. I found quite a few mistakes in the material and my confidence in it is now quite low.
My notes will be coming out at a much slower pace as I switch my course materials. Some information may be duplicated. Thanks for following along!