Category: Software
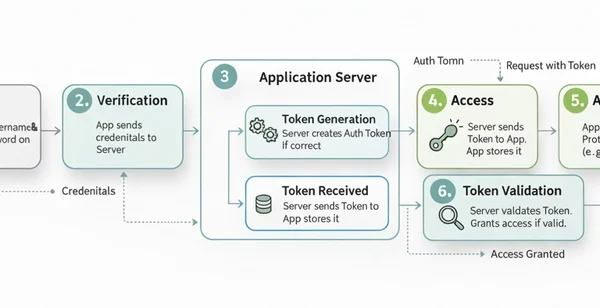
Authentication Tokens: Your Digital VIP Pass 🎫
In today’s connected world, we all want to access our favorite apps and websites without re-entering our password every two seconds. That’s where authentication tokens, or “auth tokens,” come in. Think of them like a digital VIP pass. When you log in with your username and password, the server checks your credentials and, if everything’s…

KEXP: Derya Yıldırım & Grup Şimşek – Cool Hand (Live on KEXP)
Derya Yıldırım & Grup Şimşek brought “Cool Hand” to life in a spirited live session at the KEXP studio on July 31, 2025. Fronted by Derya’s vocals and sax, the quartet features Axel Oliveres on organ, synth and bass synth, Helen Wells smashing the full drum kit and Alana Amram grooving on bass guitar—all adding…
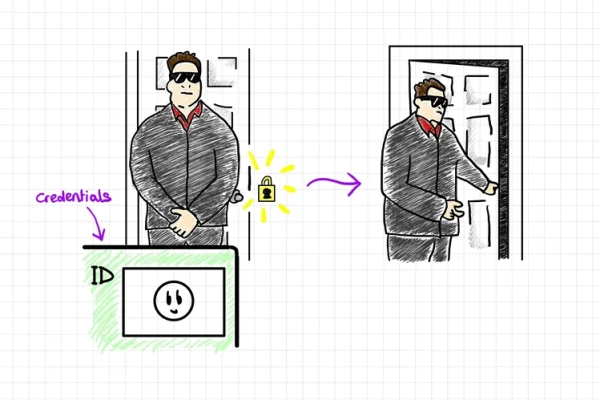
Let’s Sketch Identity: Authentication vs. Authorization
So, you are building an application and need a login form. In it, you’ll get the user’s email and password, send them to an API, and… something happens. The user is logged in afterwards. But what is that something? How does your application decide who gets in and what they get to see? This is…
No Laying Up Podcast: BallKnowers with Bob Sturm | Trap Draw, Ep 360
In Trap Draw Ep. 360, TC and Randy welcome longtime pal Bob Sturm for a spirited, team-by-team breakdown of what we’ve seen across the NFL through the first three weeks of the season—and they even give us an update on the standings in their team draft. They also plug supporting the Evans Scholars Foundation, give…

What is data modernization and why is it critical for enterprises?
Most enterprises today are sitting on petabytes of data — but much of it is locked in silos, aging warehouses, or legacy systems that simply can’t keep up. The result? Slow reporting, limited analytics, compliance headaches, and AI projects that never scale. This is where Data Modernization steps in. What is Data Modernization? At its…

My First Tauri CI/CD Pipeline: Lessons from Building VaultNote with SvelteKit
Building VaultNote: My Wild Ride with Tauri, SvelteKit, and a Hard-Fought CI/CD Pipeline Hey there, fellow devs! I’m Michael, and I’m excited to share my journey building VaultNote, a little note-taking app that’s my playground for learning cross-platform development with Tauri and SvelteKit. If you’re into JavaScript, Svelte, or just curious about building apps for…
Bankruptcy is supposed to be a safety net, not a weapon. Tyler Davis and his partners turned it into a shield for fraud, and that is a crime against all of us.
How Porter Consulting LLC Owner Tyler Davis Is Involved in Bankruptcy Proceedings Tied to Financial Crimes Marcus ・ Sep 24 #financialcrimes #bankruptcyfraud #corporatecorruption #whitecollarcrime Source link

Qualys vs ZeroThreat: Strengths, Limitations, and Use Cases
Security testing is no longer a checklist exercise; it’s a core requirement for building and running resilient software in today’s cloud-first world. With applications growing in complexity, spanning microservices, APIs, and authentication-heavy workflows, organizations need testing tools that can keep pace with constantly changing environments. Two names often come up in conversations around vulnerability detection:…
Building Your First API in Laravel – A Beginner’s Guide
APIs (Application Programming Interfaces) are the backbone of modern web and mobile applications. They allow your frontend to communicate with your backend seamlessly. If you’re new to Laravel, building your first API can seem daunting, but don’t worry – this guide will walk you through it step by step. Why Build APIs in Laravel? Laravel…

