The Linux file permissions were very complex for me at the beginning. In this article, we’ll break down Linux permissions in detail. I’ll try to make it as simple as possible.
Why Permissions Matter
Linux is a multi-user system. Even on your personal computer, system processes, services, and your own account interact with files. Permissions ensure:
- Sensitive files can’t be read or edited by the wrong users.
- Scripts and binaries are only run when explicitly allowed.
- System stability and security are preserved.
The Three Permission Types
Every file and directory in Linux can have three kinds of permissions:
- Read (r) → View the file contents or list directory contents.
- Write (w) → Modify or delete the file, or create/remove files in a directory.
- Execute (x) → Run the file as a program/script, or enter a directory.
Who Permissions Apply To
Permissions are assigned to three categories of users:
- User (u) → the file’s owner.
- Group (g) → the group assigned to the file.
- Others (o) → everyone else.
Viewing Permissions
You can check file permissions with ls -l:
ls -l script.sh
Example output:
-rwxr-xr-x 1 root root 40 Sep 23 15:15 script.sh
Breaking it down:
-
-→ file type (a dash means a regular file;dwould mean directory). -
rwx→ user (owner) can read, write, execute. -
r-x→ group can read, execute. -
r-x→ others can read, execute.
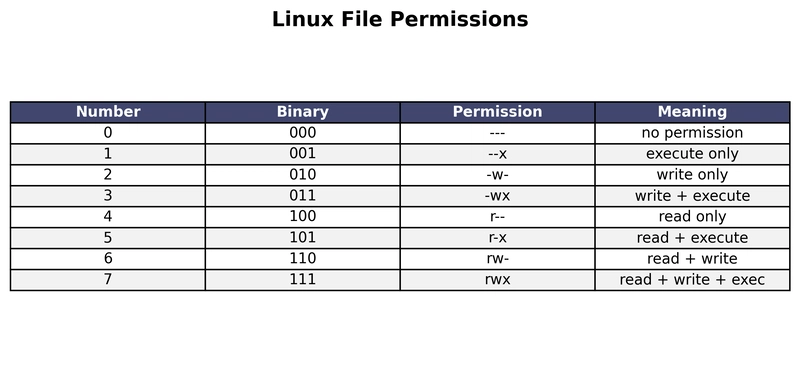
Numeric (Octal) Permissions
Permissions are often set with numbers using the chmod command. Each permission corresponds to a binary bit:
- Read = 4 (100)
- Write = 2 (010)
- Execute = 1 (001)
You add them up to set a value from 0–7:
| Number | Binary | Permission | Meaning |
|---|---|---|---|
| 0 | 000 | — | no permission |
| 1 | 001 | –x | execute only |
| 2 | 010 | -w- | write only |
| 3 | 011 | -wx | write + execute |
| 4 | 100 | r– | read only |
| 5 | 101 | r-x | read + execute |
| 6 | 110 | rw- | read + write |
| 7 | 111 | rwx | read + write + exec |
Examples
- chmod 755 script.sh
- User:
7 = rwx→ full permission - Group:
5 = r-x→ read + execute - Others:
5 = r-x→ read + execute - Result:
-rwxr-xr-x
- chmod 644 notes.txt
- User:
6 = rw-→ read + write - Group:
4 = r--→ read only - Others:
4 = r--→ read only - Result:
-rw-r--r--
- chmod 777 file.sh
- Everyone has read, write, and execute.
- Result:
-rwxrwxrwx - ⚠️ Usually not safe in real systems.
Symbolic Permissions
Instead of numbers, you can also set permissions symbolically:
-
chmod u+x file.sh→ add execute for user -
chmod g-w file.sh→ remove write for group -
chmod o+r file.sh→ add read for others -
chmod a+x file.sh→ add execute for all (user, group, others)
Best Practices
- Use 755 for scripts and executables → owner full, others can run but not modify.
- Use 644 for text or config files → owner can edit, others can only read.
- Avoid 777 unless it’s a temporary or testing environment.
- Remember directories need execute (x) to be entered (
cd).
Conclusion
Linux file permissions are not as intimidating as they look. They’re simply a combination of read (4), write (2), execute (1) applied to user, group, others.
If you can read a permission string like -rwxr-xr-x and understand what it means, you’ve unlocked one of the most fundamental skills in Linux system administration.