Over-the-Air (OTA) updates are vital in modern IoT deployments. As of 2024, over 17 billion connected IoT devices are in use globally, and this number is expected to grow to 29 billion by 2030 (Statista). With such scale, manually updating firmware is no longer practical. OTA mechanisms allow for remote updates, reducing operational costs, improving security, and increasing device longevity.
For any IoT Development Company or IoT Solutions Provider, mastering OTA implementation is essential. This article outlines three proven OTA update methods, explains how they work, and highlights key considerations for secure and reliable deployment.
What Is OTA in IoT?
OTA (Over-the-Air) refers to the wireless delivery of software, firmware, or configuration updates to devices. It’s commonly used in smartphones, but it’s equally important in the Internet of Things.
Why Is OTA Crucial?
- Remote maintenance: Fix bugs or update features without physical access.
- Security: Patch vulnerabilities across fleets quickly.
- Scalability: Manage thousands or millions of devices efficiently.
Three Reliable Methods to Implement OTA in IoT Devices
There is no universal approach to OTA. Choosing the right method depends on hardware, connectivity, power constraints, and the use case. Below are three widely-used OTA update methods:
1. Full Firmware Replacement
This is the simplest form of OTA, where the entire firmware image is replaced with a new version.
How It Works:
- A server stores the new firmware version.
- The device downloads the entire image.
- After validation, the device replaces the old firmware.
- A reboot applies the changes.
Advantages:
- Simpler to implement.
- Easier version control.
Disadvantages:
- Large bandwidth usage.
- Longer update time.
- Higher risk of bricking if interrupted.
Use Cases:
- Small-scale deployments.
- Devices with high-speed connections.
- Scenarios where update size is not critical.
Key Considerations:
2. Delta or Binary Difference Updates
Instead of replacing the whole firmware, only the differences (or “diffs”) between the old and new versions are sent.
How It Works:
- The server generates a binary diff patch.
- The device downloads the patch.
- The patch is applied to the existing firmware.
- The new version is reconstructed and activated.
Advantages:
- Reduced data usage.
- Faster updates.
- Lower battery consumption.
Disadvantages:
- Requires more complex implementation.
- Patch generation must be accurate.
- Error handling is more critical.
Use Cases:
- Battery-powered devices.
- Devices with limited bandwidth (e.g., LoRaWAN, NB-IoT).
- Environments with intermittent connectivity.
- Example: Delta Patch Process
- Modular or Component-Based Updates
Instead of updating the entire firmware, only specific modules or components are updated.
How It Works:
Firmware is designed in separate modules (e.g., network stack, sensor drivers).
Each module can be updated independently.
Update only the affected components.
Advantages:
- Very low data consumption.
- Fine-grained control.
- Isolated testing of components.
Disadvantages:
- Complex system architecture.
- Version compatibility between modules must be maintained.
- Requires precise dependency management.
Use Cases:
- High-end IoT devices with modular software architecture.
- Long-lifecycle products needing frequent feature updates.
- Industrial IoT (IIoT) with strict validation requirements.
Choosing the Right OTA Method
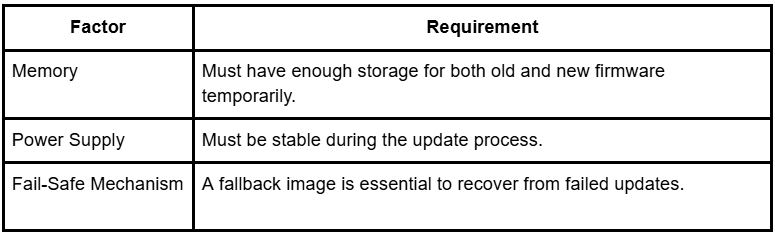
Selection depends on the following factors:
Security Considerations for OTA Updates
Security is critical when managing remote updates. OTA channels are a prime target for attackers. Poor implementations can lead to bricked devices or exploited vulnerabilities.
Essential Security Practices
- Cryptographic Signing: Every firmware or patch must be signed using public-key cryptography. Devices verify this before installing.
- **Encrypted Communication: **Use TLS or DTLS to protect firmware during transmission.
- Device Authentication: Devices must authenticate with the server before requesting updates.
- **Rollback Protection: **Prevent re-installing older, vulnerable firmware.
- Integrity Checks: Use hashing (e.g., SHA-256) to validate downloaded files.
Common OTA Protocols and Tools
There are several protocols and platforms available for implementing OTA updates.
Popular OTA Protocols
OTA Implementation Lifecycle
Understanding the lifecycle helps build a robust OTA infrastructure.
1. Build Firmware with OTA Support
- Include dual-partition layout (active and standby).
- Implement bootloader with rollback logic.
- Integrate update client libraries.
2. Push Update to Server
Upload firmware to the update server.
Sign the firmware image.
Define device groups and version rules.
3. Trigger and Monitor Update
- Devices periodically check for updates.
- Download and verify.
- Apply update, reboot, and validate.
- Report success or failure.
Challenges in OTA Implementation
Implementing OTA updates comes with several challenges:
- Device Heterogeneity: Multiple hardware variants require tailored updates.
- Network Reliability: Poor connections lead to failed updates.
- Power Failures: Unexpected power loss during update may brick devices.
- Version Management: Compatibility between firmware and modules must be ensured.
Role of IoT Development Companies and IoT Solutions Providers
A trusted IoT Development Company plays a critical role in implementing OTA strategies. Their responsibilities include:
- Designing firmware with OTA readiness.
- Choosing the appropriate OTA method.
- Setting up secure update servers.
- Managing update rollouts.
- Ensuring compliance with industry standards (e.g., ISO 30141, NIST).
Final Thoughts
OTA updates are a non-negotiable feature in any serious IoT deployment. Selecting the right method—full firmware, delta update, or modular update—depends on your device capabilities and application needs. Prioritize secure communication, robust fail-safes, and version control mechanisms.
An experienced IoT Solutions Provider ensures these elements are in place, delivering long-term device reliability and user trust. Whether you manage 10 devices or 10 million, mastering OTA is essential for secure, maintainable, and scalable IoT solutions.
FAQs
Q1: Can OTA be used in low-power devices?
Yes. Delta and modular updates are better suited for low-power or battery-operated devices.
Q2: Is OTA possible over LoRa or NB-IoT?
Yes, but use compressed delta updates and chunked transfers due to limited bandwidth.
Q3: What happens if an update fails?
A well-designed OTA system should support rollback to a previous working firmware version.