Large Language Models for One-Day Vulnerability Detection
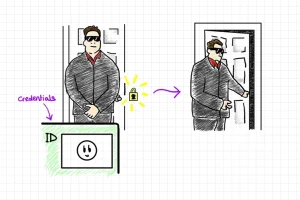
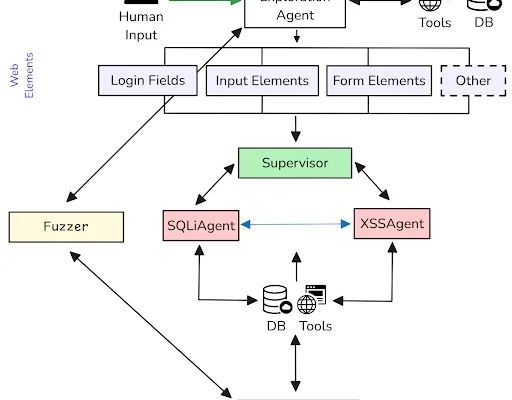
Hello fellow cybersecurity professionals and enthusiasts, In this article, I will share my graduate capstone project titled Large Language Models for One-Day Vulnerability Detection that details an innovative penetration testing framework that incorporates natural language processing and large language model (LLM) driven multi-agent systems to automate and expedite one-day vulnerability detection. Problem New software vulnerabilities…