Scenario
My organization needed workloads to communicate using domain names instead of raw IP addresses. The requirement was to avoid setting up a custom DNS solution and rely solely on Azure-native DNS services.
To meet this, we implemented:
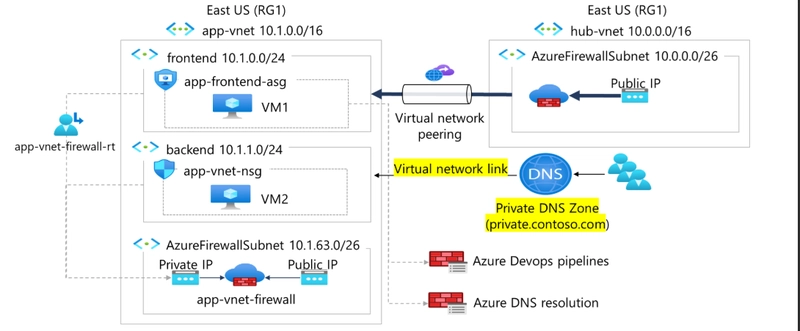
A Private DNS zone (private.contoso.com)
A Virtual network link to app-vnet
A new DNS record for backend resources
This setup provides secure, reliable, and simplified workload communication within Azure virtual networks.
Skilling Tasks
Create and configure a Private DNS zone
Link the DNS zone to a Virtual Network
Add and manage DNS record sets
Configure DNS settings on a virtual network
Architecture Diagram
Step-by-Step Implementation
- Create a Private DNS Zone
In the Azure portal, search for Private DNS zones.
Click + Create and configure:
Resource Group: RG1
Name: private.contoso.com
Region: East US
Select Review + Create → Create.
This creates a secure DNS zone for internal name resolution.
- Create a Virtual Network Link
To ensure workloads in app-vnet can resolve names from this DNS zone:
Open your private.contoso.com DNS zone.
In the DNS Management blade, select + Virtual network links.
Configure:
Link name: app-vnet-link
Virtual network: app-vnet
Enable auto registration: Enabled
Click Create.
Now, VMs in app-vnet can auto-register and resolve DNS names.
- Create a DNS Record Set
Finally, we add a record for the backend workload:
Open the private.contoso.com DNS zone.
Select + Record set.
Configure:
Name: backend
Type: A
TTL: 1
IP Address: 10.1.1.5
Now, workloads can resolve backend.private.contoso.com → 10.1.1.5.
Key Takeaways
Azure Private DNS zones provide a built-in way to manage DNS for private workloads.
Virtual network links allow seamless DNS resolution across VNets.
DNS record sets simplify internal communication without exposing workloads publicly.
This exercise reinforced my skills in Azure networking, DNS configuration, and workload security—a crucial part of designing cloud-native architectures.