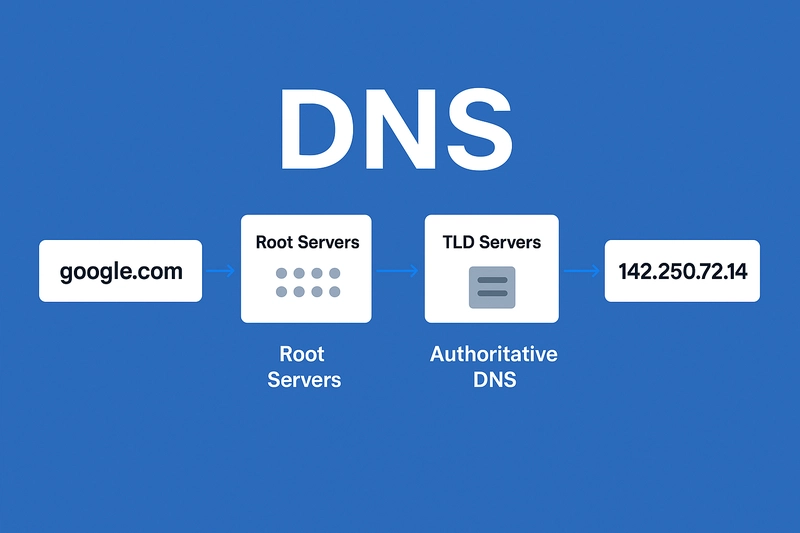
When you type google.com in your browser, it feels instant. But behind the scenes, there’s a powerful system mapping human-readable domains to machine-friendly IPs: DNS (Domain Name System).
For DevOps engineers, DNS is more than just theory—it’s at the heart of application availability, cluster networking, and troubleshooting. Let’s break down how DNS works and why it matters in real-world DevOps.
🔑 1. Root Servers – The Internet’s Directory
Every DNS query starts with the root servers.
There are 13 named root server clusters (A–M), but thanks to anycast, they exist as hundreds of distributed servers worldwide.
Here’s the step-by-step flow when you query google.com:
-
Browser/OS Check: Browser checks cache, OS cache, and
/etc/hosts. If no record, it queries the configured resolver (e.g., 8.8.8.8). -
Recursive Resolver → Root Server: Resolver doesn’t know
google.com, so it asks a root server. -
Root Server Response: Root server says, “I don’t know google.com, but I know who manages
.com. Go ask the.comTLD server.” -
TLD Server:
.comserver responds, “I don’t know the IP, but here’s the authoritative server for google.com.” -
Authoritative Server: Google’s DNS replies: “
google.com= 142.250.72.14.” - Final Step: Resolver caches it, and your browser connects directly to that IP.
📌 DevOps Use Case:
If you deploy myapp.dev on AWS and configure it in Route53, DNS propagation follows this chain. A single misstep (e.g., wrong nameserver delegation) = app unreachable. Tools like dig or nslookup help trace where it fails.
🔑 2. Anycasting of Root Servers – Why DNS is Fast & Resilient
Root servers aren’t single machines. They use anycast routing:
- Multiple servers worldwide share the same IP address.
- When you query, BGP routing ensures you hit the closest available root server.
- This reduces latency and increases fault tolerance.
📌 DevOps Use Case:
For global apps (deployed in Mumbai + Virginia), anycasting ensures users always hit the nearest DNS server, speeding up requests. Without it, DNS would be a massive bottleneck.
🔑 3. Port 53 – The Gateway for DNS
DNS typically uses port 53:
- UDP/53 → Default for queries (fast, lightweight).
- TCP/53 → Used if the response is too large (e.g., DNSSEC, zone transfers).
📌 DevOps Use Case:
If your firewall or Kubernetes NetworkPolicy blocks port 53, pods can’t resolve domains (curl google.com fails inside containers). Always check port 53 when debugging DNS issues in clusters.
🔑 4. resolv.conf – The Resolver Configuration
On Linux/macOS, /etc/resolv.conf tells your system which DNS servers to use.
Example:
nameserver 8.8.8.8 # Google DNS
nameserver 1.1.1.1 # Cloudflare DNS
search default.svc.cluster.local
- The
nameserverlines specify where queries go first. - The
searchdirective is critical in Kubernetes:- You can just run
ping myservicein a pod. - Behind the scenes, it expands to
myservice.default.svc.cluster.local.
- You can just run
📌 DevOps Use Case:
If services in Kubernetes aren’t resolving, check /etc/resolv.conf inside pods. Misconfigured search domains break service discovery.
🔑 5. hosts File – Manual Overrides
The /etc/hosts file maps hostnames to IP addresses before DNS is queried.
Example:
127.0.0.1 localhost
192.168.1.10 staging.myapp.dev
- Checked before DNS lookup.
- Useful for local testing and overrides.
📌 DevOps Use Case:
- Point
staging.myapp.devto a local IP for testing before DNS propagation. - Override domains during CI/CD pipeline testing.
- Debug DNS by bypassing external resolvers.
🔑 6. Bonus: Other Important DNS Concepts
- Recursive Resolvers → Google DNS (8.8.8.8), Cloudflare DNS (1.1.1.1), or your ISP.
- Authoritative Servers → Store the final answer for a domain (managed via Route53, Cloudflare, GoDaddy, etc.).
- DNS Caching → Reduces latency, but wrong TTL = stale records.
- DNS Propagation → Global delay when records change (can take minutes to hours).
⚡ Real-World Scenarios Where DNS Breaks DevOps
- Pods can’t resolve services → CoreDNS misconfigured in Kubernetes.
- App deployed but unreachable → DNS record missing or not propagated. 👉 Coming up next in my Advanced DevOps series: “Kubernetes Networking Demystified: From Pod-to-Pod Communication to Ingress”.
- SSL cert failure → Domain points to wrong IP.
- Multi-region latency → Not using latency-based DNS routing (Route53, Cloudflare).
-
CI/CD tests failing → Use
/etc/hostsoverride to simulate new environments.
✅ Conclusion
DNS is the hidden backbone of the internet. For DevOps engineers, understanding root servers, anycast, port 53, resolv.conf, and hosts is more than academic—it’s practical.
The next time a pod can’t reach a service or your new domain fails to resolve, you’ll know exactly where to look in the chain.